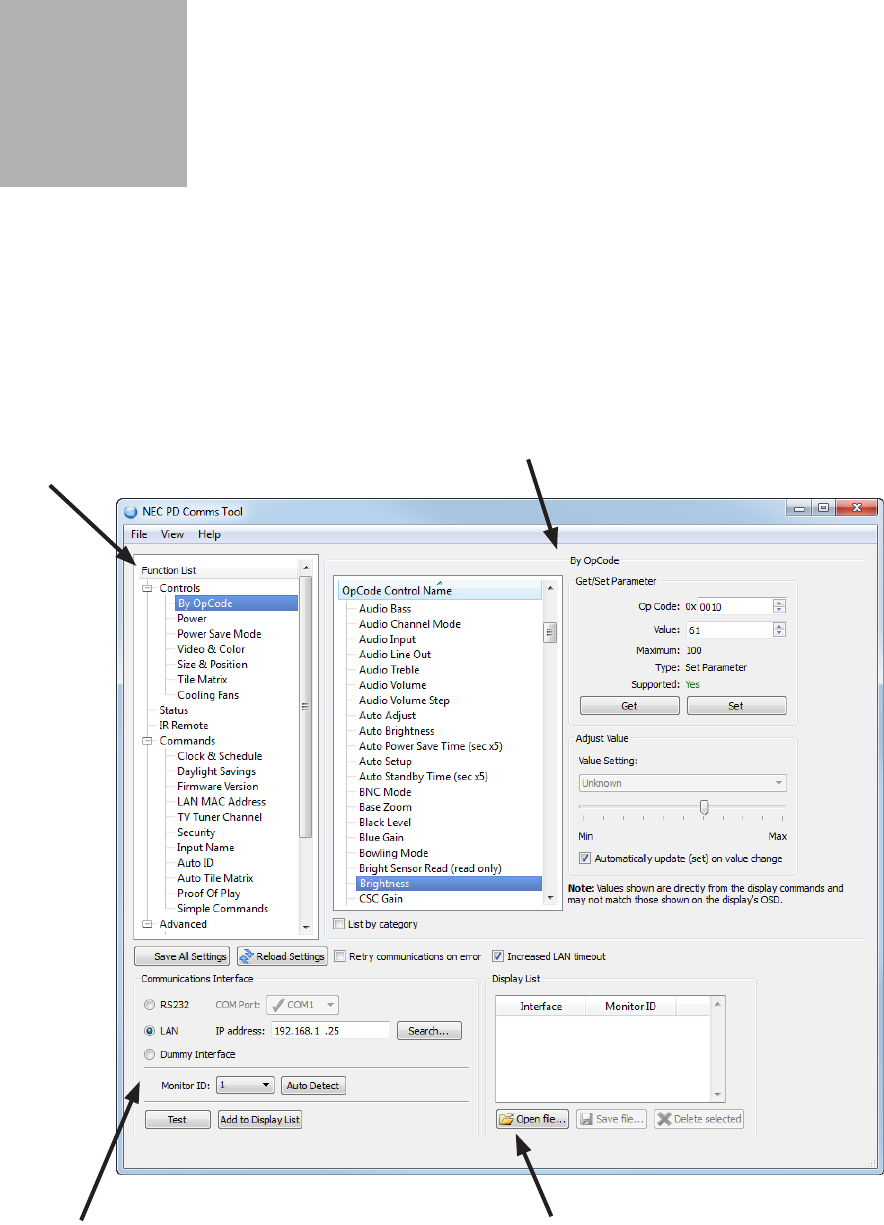
Opcode Sequences As Representation of Executables For Data-Mining-Based Unknown Malware Detection (Elsevier-2013) PDF | PDF | Cross Validation (Statistics) | Machine Learning
Unknown command" error when trying to debug a python script on open folder context · Issue #4070 · microsoft/PTVS · GitHub
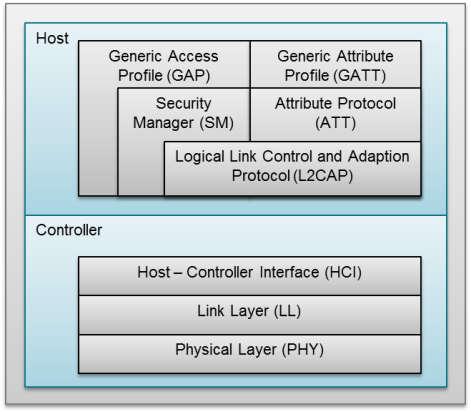
Bluetooth Low Energy Protocol Stack — Bluetooth Low Energy Software Developer's Guide 3.00.00 documentation

GFK 0467lseries90 30 20 MicroPLCCPUInstructionSetReferenceManual | PDF | Programmable Logic Controller | Input/Output

Faculty of ICT - Education, Research & Collaboration - Final Year Projects 2022 by ICT University of Malta - Issuu
Test failure JIT/opt/Devirtualization/structreturningstruct/structreturningstruct.sh · Issue #66924 · dotnet/runtime · GitHub
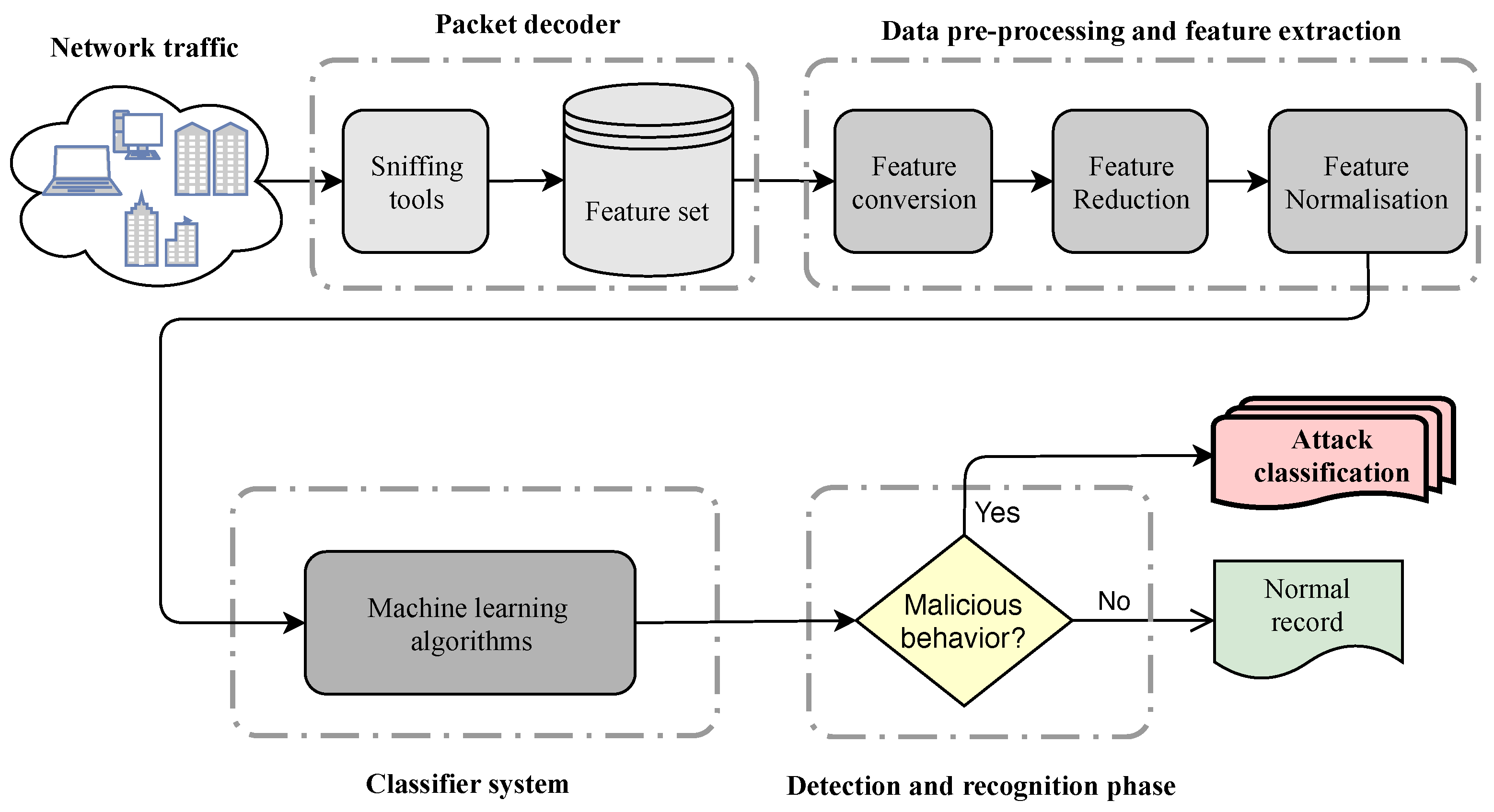
Entropy | Free Full-Text | A Review on Machine Learning Approaches for Network Malicious Behavior Detection in Emerging Technologies
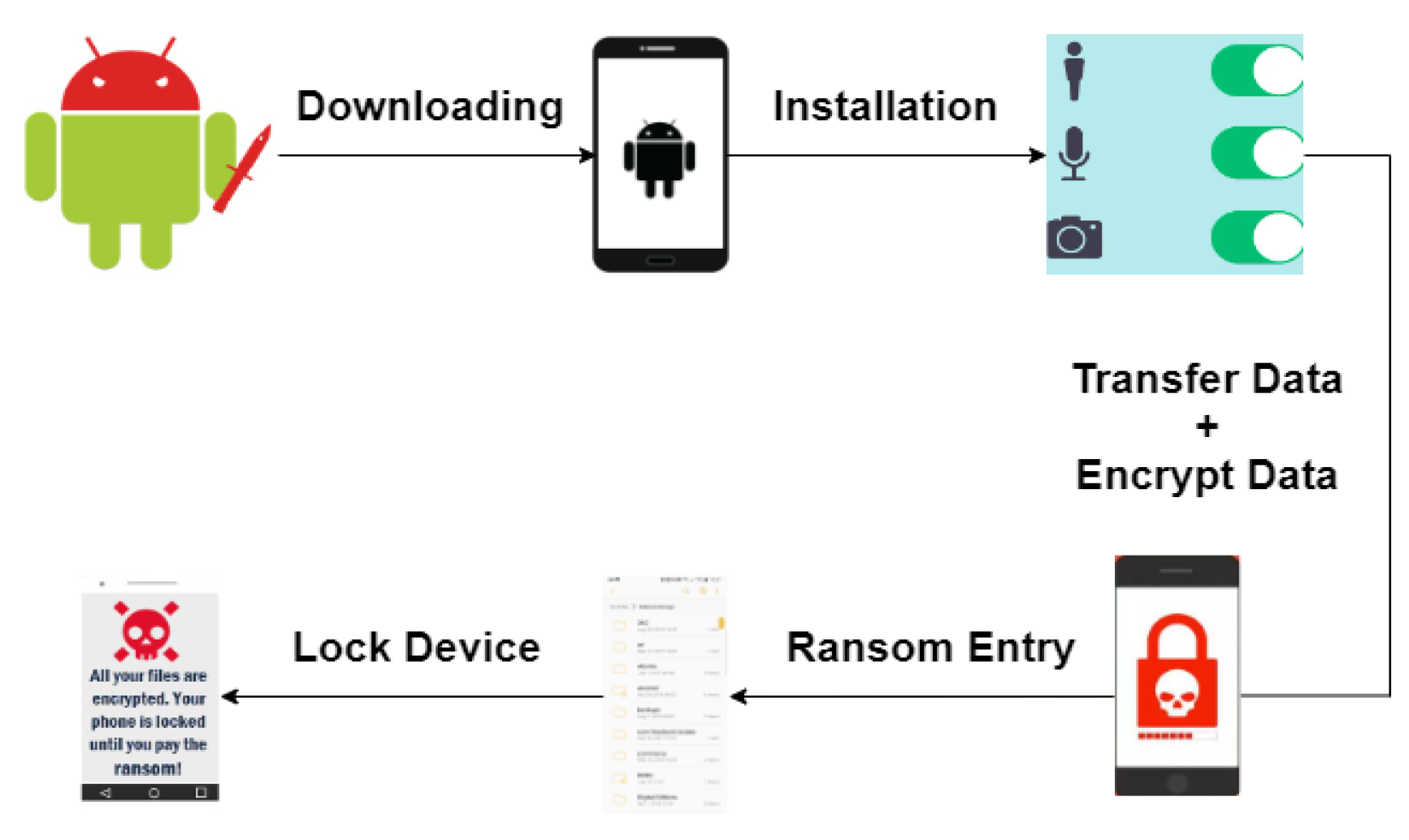
Information | Free Full-Text | The Effect of the Ransomware Dataset Age on the Detection Accuracy of Machine Learning Models
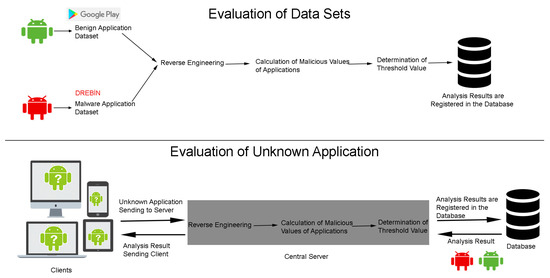
Applied Sciences | Free Full-Text | Web-Based Android Malicious Software Detection and Classification System
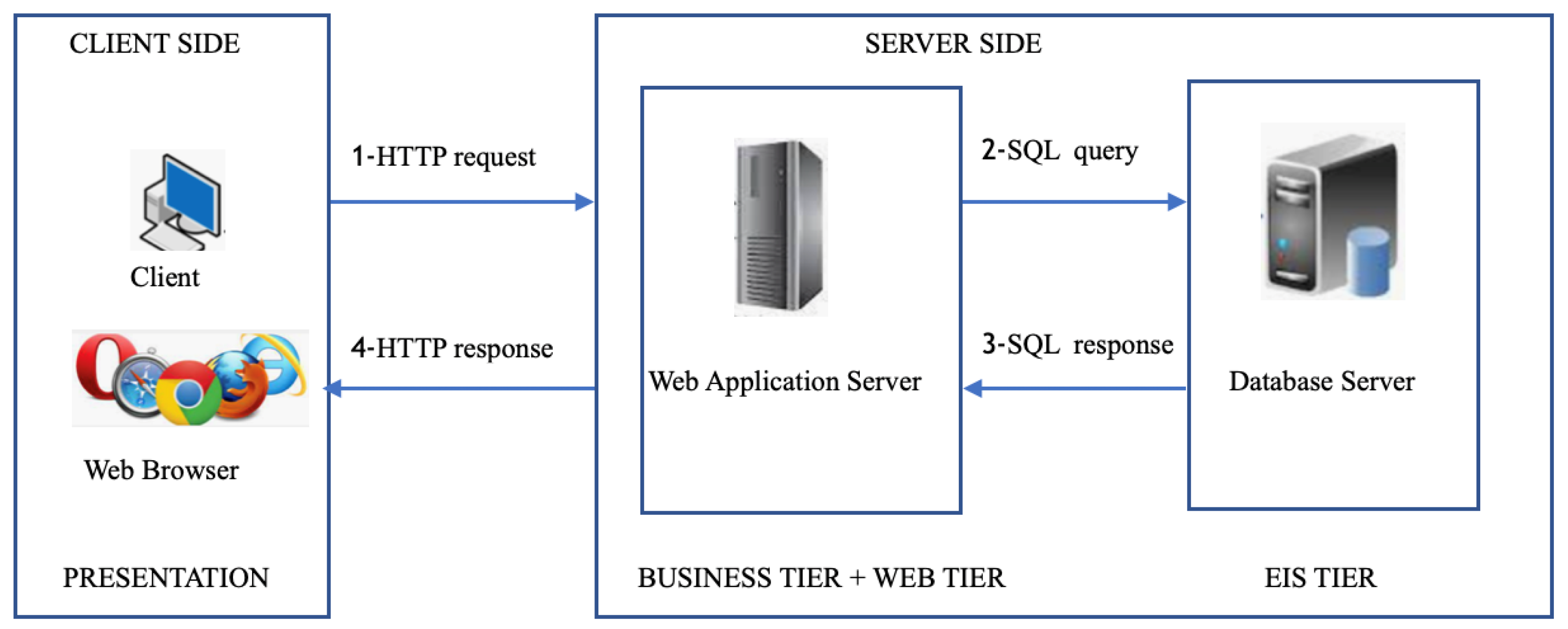
![PDF] PDF-Malware: An Overview on Threats, Detection and Evasion Attacks | Semantic Scholar PDF] PDF-Malware: An Overview on Threats, Detection and Evasion Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f6fd3f88d2aa6959b042dc92c22719243e48404a/4-Figure4-1.png)